Authentication#
Authentication is the process of verifying the identity of an agent. To access private data on Solid Pods, you must authenticate as a user/agent who has been granted appropriate access to that data.
Authentication Flows#
Solid authentication is based on the Solid-OIDC specification. Solid-OIDC builds upon the OpenID Connect standards, which itself builds on the OAuth 2.0 authorization framework.
For applications implementing Authorization Code Flow:
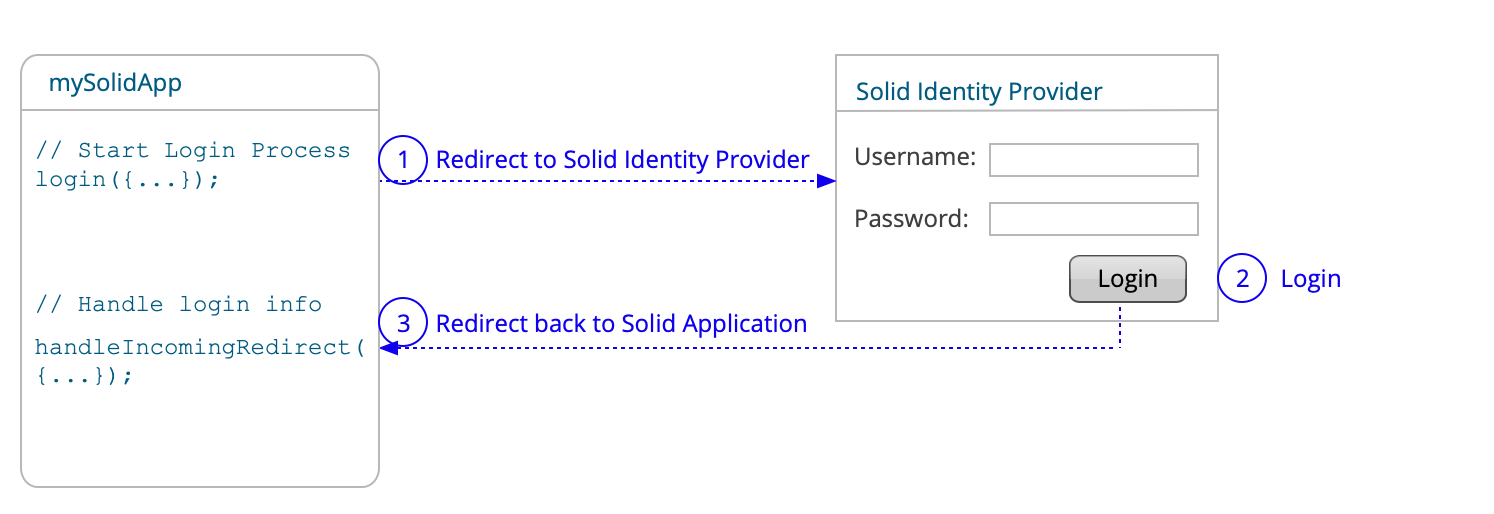
The application starts the login process by sending the user to the user’s Solid Identity Provider.
The user logs in to the Solid Identity Provider.
The Solid Identity Provider sends the user back to your application, where the application handles the returned authentication information to complete the login process.
For applications implementing Client Credentials flow:
The application (such as a single-user script) logs in, on behalf of the user who registered the client, by sending its client credentials to its Solid Identity Provider (i.e., where the user registered the client).
The Solid Identity Provider returns the tokens to the app.
Inrupt Client Libraries#
Inrupt provides the following libraries for authentication:
@inrupt/solid-client-authn-browserto authenticate in a browser.@inrupt/solid-client-authn-nodeto authenticate in Node.js.
Note about Client IDs
In Solid-OIDC (i.e., in OAuth 2.0 and OpenID Connect), an application identifies itself using a client identifier (Client ID).
A Client ID can be:
a URL that dereferences to a Client ID Document.
a value that has been registered using either OIDC dynamic or static registration.
Inrupt’s client libraries provide login APIs that supports:
Specifying a Client ID (of type URL) that dereferences to a Client ID Document.
Logging in with client credentials (Client ID and Secret) from static registration.